Some of the security factors to be considered for cloud adoption includes
- Protection of intellectual property:
A McAfee analysis found that 21% of the files uploaded to file-sharing services contained sensitive data related to intellectual property. There is a considerable risk associated with BYOC in which the organizations don’t know what information and intellectual properties are exposed. Certain services of the cloud providers and the third parties can pose a risk if the terms and conditions are not framed properly, which allows them legal immunity to get rights over your intellectual property.
- Compliance adherence:
Companies should operate under the mandate of regulatory controls of their information. Enforcement of HIPAA, FERPA, and other regulations enables the companies to know where are their data located, who has access to the data and how security measures and configuration set-ups are being employed to protect it. With BYOC, there are greater chances of violations of these regulations, putting the organization in jeopardy and a state of non-compliance.
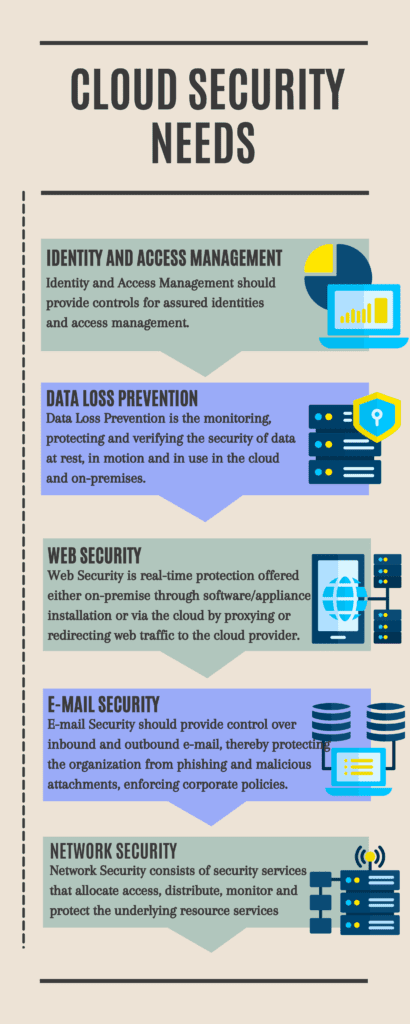
- Role based access control
Companies must have proper control over end-user access and actions. Creating a control framework for the users may lead to theft, breaches, and infringements on the company’s data. For example, a worker resigning from the company may download vital data or clients and customers, upload the data onto a cloud storage service, and use that information when employed by the competitor. So, role-based access control must be in place, limiting user access.
- Contractual agreements with business partners
In the contractual agreement with business partners, the migration clause of vital data or other additional actions required to move to the cloud must be enlisted. This would stop the chances of conflict and provide better visibility to the partners of how data and other services are being secured. It would also help stop any third-party violations.
Ready to experience the full power of cloud technology?
Our cloud experts will speed up cloud deployment, and make your business more efficient.
- Encryption of systems and data
Encryption is a must for preventing breaches in your cloud infrastructure. You should ensure that your cloud vendor uses the hardware’s FIPS 140-2 level certified security model. This level 4 certification allows higher protection against infringement. Ensure that you have end-to-end and on-transit encryption for your data and devices. Restrict access to the encryption keys with role-based access.
- Sovereignty of data
According to Tech Target, “Verifying that data exists only at allowed locations can be difficult. It requires the cloud customer to trust that their cloud provider is completely honest and open about hosting their servers and adhere strictly to several level agreements (SLAs). Ensure that it complies with the regulations for data sovereignty through proper geofencing of workloads running in assigned servers.
iSmile technologies offers free consultation with an expert, talk with an expert now