Vulnerabilities are weaknesses in an organization’s security that attackers can exploit to gain unauthorized access to sensitive information or disrupt operations. Remediating vulnerability is a critical aspect of an organization’s cybersecurity strategy. It involves identifying, analyzing, and addressing security weaknesses to reduce the risk of successful cyber-attacks. In this blog, we will explore the process of how to remediate vulnerabilities, including understanding the vulnerability, identifying the cause, developing a remediation plan, implementing the solution, verifying the effectiveness, documenting and communicating the remediation, ongoing maintenance and monitoring, and best practices for preventing future vulnerabilities.
Understanding the Vulnerability
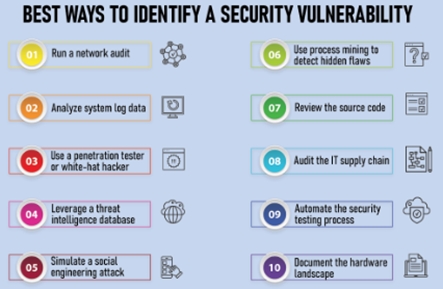
The first step in remediating a vulnerability is understanding what it is and how it can be exploited. This includes identifying the type of vulnerability, the systems and applications affected, and the potential impact on the organization. It is essential to understand the severity of the vulnerability and the likelihood of it being exploited, as this will help to prioritize the remediation efforts. Common types of vulnerabilities include software bugs, misconfigurations, and outdated software.
Identifying the Cause
Once the vulnerability is understood, the next step is identifying the cause. This could include a software bug, a misconfiguration, or outdated software. Identifying the root cause of the vulnerability is essential so that it can be addressed at its source and not just the symptoms. This will help prevent the vulnerability from recurring in the future.
Developing a Remediation Plan
Once the cause of the vulnerability has been identified, the next step is to develop a remediation plan. This plan should include details on how the vulnerability will be addressed, including the specific actions that will be taken and the timeline for completion. The plan should also include contingencies in case the initial efforts are unsuccessful. It is essential to involve the relevant stakeholders in developing the remediation plan to ensure that it is comprehensive and addresses all concerns.
Implementing the Solution
Once the remediation plan has been developed, the next step is to implement the solution. This may include applying software patches, making configuration changes, or upgrading software. It is essential to test the solution in a non-production environment before implementing it in production to ensure that it does not cause any unintended consequences.
Verifying the Effectiveness
After the solution has been implemented, it is crucial to verify its effectiveness. This may include running vulnerability scans and penetration tests to ensure that the vulnerability has been successfully addressed. It is also essential to monitor the systems and applications affected by the vulnerability to ensure that they are functioning as expected.
Documenting and Communicating the Remediation
Documenting the remediation process, including the vulnerability, the cause, the remediation plan, and the steps taken to implement the solution, is essential. This documentation should be shared with relevant stakeholders, including IT, security, and compliance teams. As required, it is also essential to communicate the remediation to external parties, such as customers or regulatory bodies.
Need cloud security advice?
Our experts will help you in reinforcing your defense strategy with the cloud.
Ongoing Maintenance and Monitoring
Remediating vulnerabilities is an ongoing process and requires ongoing maintenance and monitoring. This includes staying up to date with the latest security patches, monitoring for new vulnerabilities, and performing regular vulnerability assessments to ensure that no new vulnerabilities have been introduced. It is also essential to keep the documentation and communication of the remediation process up-to-date and to review it regularly to ensure that it is still accurate and relevant.
Best Practices for Preventing Future Vulnerabilities
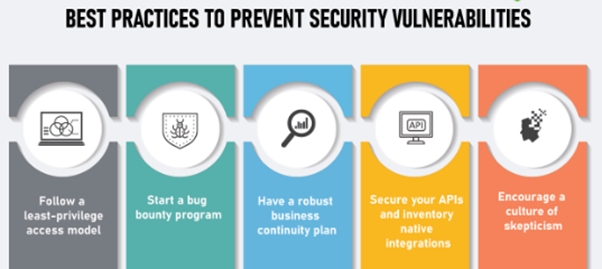
Preventing future vulnerabilities is an essential aspect of an organization’s cybersecurity strategy. To prevent future vulnerabilities, organizations should implement best practices such as:
- Keeping software and systems up-to-date with the latest security patches
- Regularly monitoring and assessing systems and applications for vulnerabilities
- Implementing secure configuration management
- Conducting regular security awareness training for employees
- Implementing intrusion detection and prevention systems
- Regularly reviewing and updating security policies and procedures
Conclusion
Remediating vulnerability is an essential aspect of an organization’s cybersecurity strategy. By understanding the vulnerability, identifying the cause, developing a remediation plan, implementing the solution, verifying the effectiveness, documenting and communicating the remediation, ongoing maintenance and monitoring, and implementing best practices for preventing future vulnerabilities, organizations can reduce the risk of successful cyber-attacks. A comprehensive and well-executed vulnerability management program is essential for organizations to protect themselves from cybersecurity threats.
ISmile Technologies helps you to maximize cloud confidence with secured cloud assets. We bring our managed cloud security services to your defense & help you reimagine cloud security by building it into the foundation of your company. Schedule your free assessment today.








