CrowdStrike Falcon Cloud Workload Protection protects all workloads, containers, and Kubernetes apps in your cloud-native stack. To make this available for all the companies, we at ISmile Technologies offer an automated security system that detects suspicious activity and zero-day assaults so enterprises can stay ahead of threats and limit the attack surface. As part of Falcon’s runtime protection, containers are protected from active assaults and can run on Linux and Kubernetes environments such as EKS.
ISmile can assist security teams in combating advanced threats against containers using machine learning, artificial intelligence, custom hash blocking, and a library of IOAs. Behavioural profiling makes it possible to restrict any activities that break policy without affecting the container’s lawful functions. Combined, these features allow the company to thwart threats beyond more traditional security measures and ensure that protection is always on.
Why Falcon cloud workload protection by ISmile Technologies?
As a result, our clients can concentrate on building their businesses while our IT experts handle all security elements. It can be challenging for companies to acquire and maintain top-notch security expertise because top-notch security talent requires ongoing challenge and development. To attract and retain the best people, ISmile Technologies places a high priority on security. Managed services allow us to pass along our knowledge and experience to our customers with the following benefits:
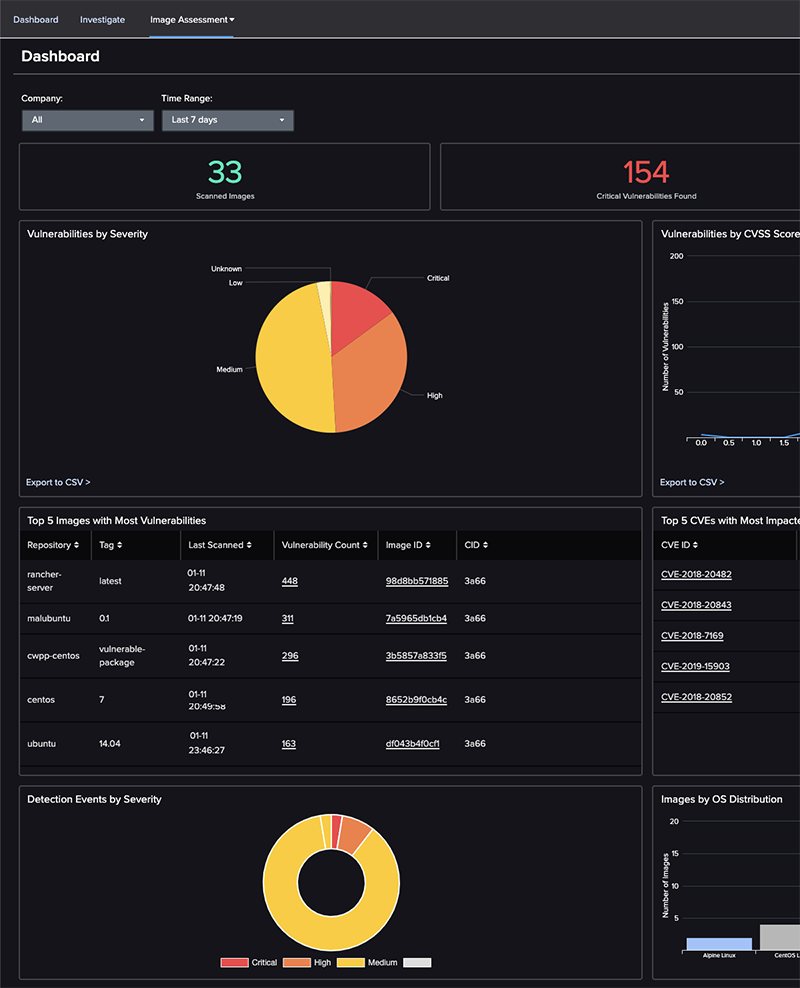
- Vulnerability Scanning and Management
Improve the quality of your judgments: Learn more about your cloud workload and containers, including images, registries, libraries, and the containers spun up from those images, to make more informed decisions.
Uncover hidden threats: Reduce the attack surface by uncovering your images’ hidden dangers such as malware, secrets, and configuration flaws.
Container environments can be viewed from the outside: Find out what files, networks, and processes are being accessed and communicated with inside running containers with complete visibility.
Identify Vulnerability Faster: Get to the bottom of security issues more quickly pre-built image scanning policies allow you to quickly identify vulnerabilities, misconfigurations, and other issues, saving you significant time.
Eliminate hazards before making the product: Eliminate problems for security teams by blocking exploitable vulnerabilities based on IOAs before runtime.
Keep an eye always: Scan images during runtime and take action without having to rescan them.
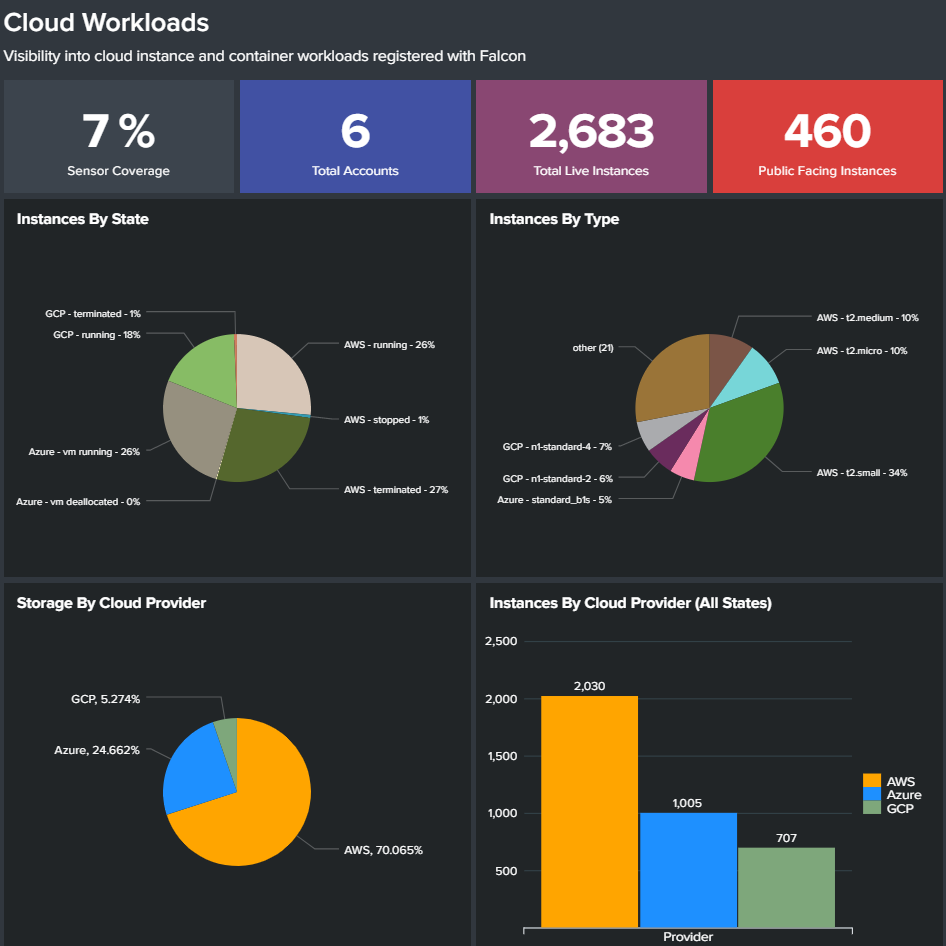
- Multi-cloud Workload Discovery
Continuous resource discovery: Provides insight into your cloud footprint so you can secure all workloads and uncover and manage risks while reducing the attack surface.
Automate discovery: AWS EC2 instances, GCP Compute instances, and Azure VMs are automatically discovered without needing an agent installed.
Granular context and insights: It provide real-time data about the workloads, including context-rich metadata about the system size and configurations, as well as networking and security group information for the AWS, GCP and Azure.
Uncover unprotected resources: Find resources that aren’t protected. The Falcon platform does not protect any of the specified workloads.
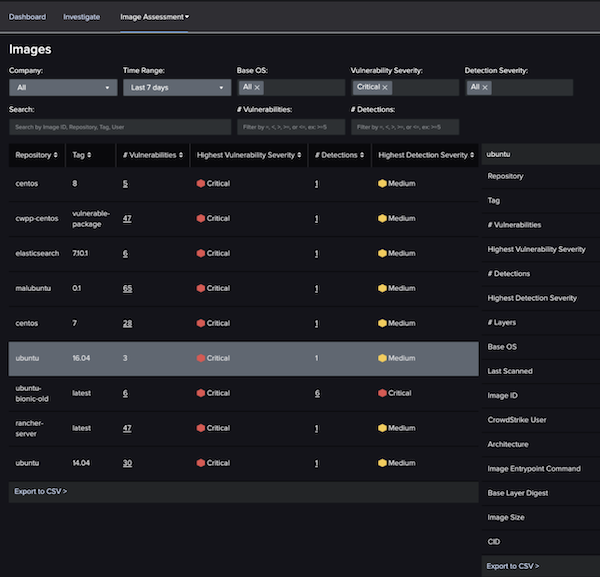
- Automated CI/CD Pipeline Security
Delivery should be sped up: Only approved images can be used in your hosts or Kubernetes clusters if you implement verified image policies to prevent them from advancing through your pipeline.
Detect dangers faster: Container images are constantly scanned for known vulnerabilities, secret/keys, and configuration concerns.
Your pipeline’s vulnerability status should be assessed: Before containers are deployed, find malware that static scanners missed.
Intensify patrols and other security measures: Contextualize and de-mystify configuration errors and regulatory violations for security operations.
Developer toolchain integration: Faster remediation and response inside the DevOps tool sets you already use, thanks to the seamless integration with Jenkins, Bamboo, GitLab and more.
Enable DevSecOps: Security operations, DevOps, and infrastructure teams benefit from better communication and coordination through dashboards and reports.
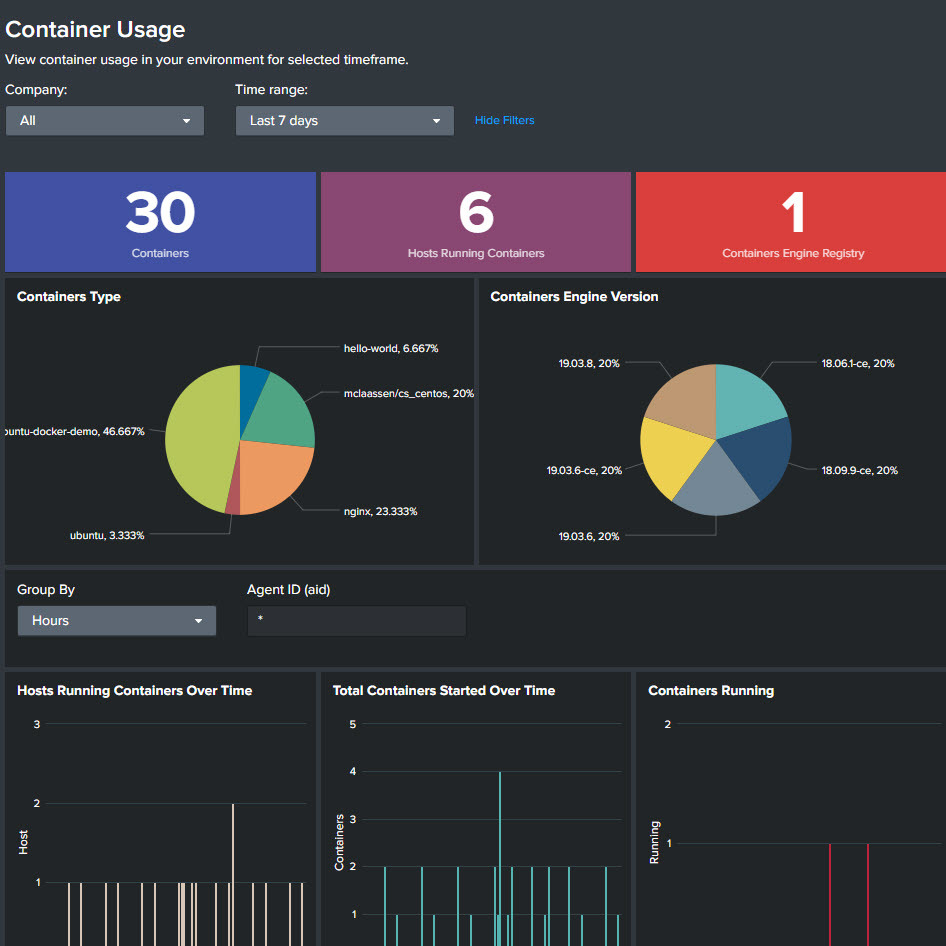
- Container Security
Complete visibility into container environment: A complete view of the container environment includes both on-premises and cloud-based containers.
Attacks against container environments should be prevented: To protect your container-based applications, it identifies hidden dangers in open-source packages and 3rd party images.
Enforce container immutability: Secure images are allowed via your pipeline and run in your Kubernetes clusters or hosts if you enforce container immutability.
Log Everything: Takes snapshots of everything inside the container, even if you just run it for a brief period.
Container use is visible: Trends and uptime, images utilized, and configuration are used to identify containers that may be dangerous or misconfigured.
Keeping hosts and containers safe is a top priority: Runtime protection is provided by a Falcon agent that runs on the host and protects containers against active threats.
Accelerate Investigations: It is much easier to investigate container problems when detections are tied directly to the relevant container rather than combined with host events.
- Runtime Protection
Secure hosts and containers: Falcon’s runtime protection shields containers against active attacks on hosts.
Linux and Kubernetes setups, such as EKS, can be supported: Support for containers, including Fargate, is available and provides the same level of security. AKS, GKE, and Red Hat OpenShift all have technology previews available.
Utilize cutting-edge security solutions: Artificial intelligence (AI), machine learning (ML), indications of attack (IOAs), and custom hash blocking all work together to keep containers safe from malware and other complex threats.
Put a stop to bad behaviour: Behavioural profiling allows you to restrict behaviours that break policy while not influencing your containers’ functionality.
Improve the speed of container-related investigations: When detections are tied to a specific container rather than the host, it is much easier to conduct an investigation.
Look around: It doesn’t matter if the container is just running for a few seconds; all events generated inside the container should be recorded.
Automated Kubernetes deployment: Include it in a Kubernetes cluster for easy deployment at scale.
Streamline the management of containers: Get all the information you need about your Kubernetes pods and namespace.
- Single Source of Truth with Powerful APIs
Single data source: Security teams can respond and investigate more quickly with a single data access point.
DevOps-ready Automation: CrowdStrike Falcon’s detection, administration, response, and intelligence capabilities may be automated via powerful APIs.
Optimize business performance: Optimize corporate performance by gaining access to enhanced security orchestration, automation, and processes.
Use CI/CD pipeline integration: Chef, Puppet, and AWS Terraform provide CI/CD integrations.
Protection at the speed of DevOps: To keep up with CI/CD and the rapid pace of DevOps, Falcon provides immediate and dynamically scalable protection via API and pre-boot scripts.

Conclusion
It’s not easy to compare the many security software providers. You’ll find that CrowdStrike has the cloud security skills necessary to tackle today’s attacks when assessing your organization’s needs.
ISmile Technologies’ approach to safeguarding cloud workloads includes detection, prevention, and interaction with DevOps technologies, allowing businesses to reap the benefits of the cloud while maintaining the highest level of security possible.
- Detection and removal of attackers to stop and prevent any dangerous components from entering
- Threat Intelligence to know what an attacker’s TTP is and avoid being caught off guard.
- Cloud hygiene and posture management protect and secure the cloud environment and maintain compliance.
- Using CI/CD security ensures that DevOps can build quickly and confidently in the cloud.
- To close the skills gap and improve detection above and beyond automation, a fully managed solution should include managed threat hunting.
With a cloud-native architecture, we ensure deliver these aspects with the speed, flexibility, and capacity needed to thwart modern attackers and stop cloud breaches. Reach out to schedule a meeting and learn more about our CrowdStrike Managed Services, Consulting, Email Security and other Managed Security capabilities.








